Cybersecurity Tips
Your digital safety matters. From checking email to accessing course materials, your Emory accounts and devices help you stay connected every day. Taking a few simple steps like recognizing suspicious messages, keeping your software updated, and using secure logins can go a long way in protecting your information. Explore tips and resources designed to help you stay safe online and worry less about security, so you can focus on what’s most important your success at Emory.
Learn more about protecting your accounts and devices.
- Use a unique password for every account (consider using a password manager to help).
- Never share or reuse passwords, including with Artificial Intelligence tools.
- Change your passwords regularly. You can update your Emory password at https://mypassword.emory.edu.
- Use multi-factor authentication whenever available. At Emory, we require Duo Security two-factor authentication for multiple services. Be sure to enroll using the Duo Mobile Option for your smartphone, which will allow continued access to your Emory account as long as you have that device (even if your phone number changes!).
- Do not open emails or attachments from unfamiliar or unexpected senders.
- Critically evaluate messages: examine the email address of the sender, hover your mouse over links to check their validity, and look for misspellings or other indicators of potential illegitimacy.
- Never provide your credentials in response to an email. Reputable organizations, including Emory, will never ask you to share your password with anyone.
- If you think an email to your Emory account is a phishing attempt, report it by using the “Cofense Reporter” or “Report Phishing” options in your email client. Learn more at https://it.emory.edu/security/policies-procedures/reporting-emails.html
- Current phishing emails include unexpected job offers to students. Learn more and be on the alert!
- Operating Systems (Macs, Windows, etc.) require updates that often include the latest security measures for your device. Stay current.
- Follow data storage best practices for your important files: https://researchdata.emory.edu/store/storing-data
- Check your privacy settings under all social media accounts and consider restricting access to your posts to trusted friends and family only.
- Check your privacy settings in web browsers and apps and know how your personal data is being collected, used, and disclosed.
- Learn more: https://consumer.ftc.gov/features/protecting-your-privacy-online.
Phishing Test: Would You Take the Bait?

Here are real email examples that show how scammers impersonate trusted people and services to trick you into clicking links or sharing information.
By reviewing these examples, you’ll learn how to spot the warning signs and protect yourself from these attacks.
THE BAIT:
Trick users into entering their NetID and password into a fake form.
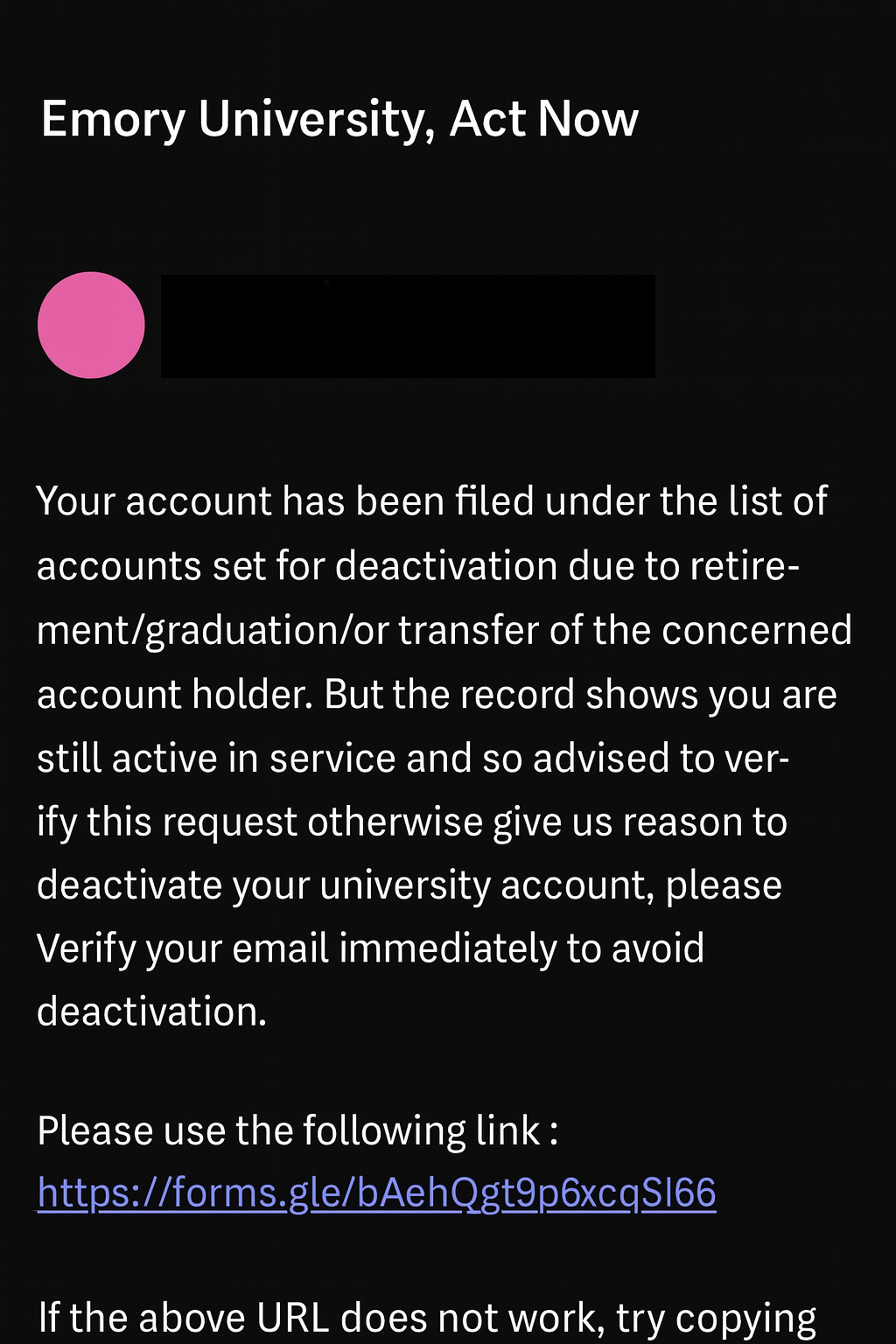
The email claims the recipient’s university account is scheduled for deactivation and urges them to “verify” immediately using a provided link.
Type of Phishing Attack
- Credential Harvesting via Account Compromise
- Goal: Trick users into entering their NetID and password into a fake form.
- Method: Use a compromised student account to send messages that appear authentic.
- Risk: Attackers expand their access to more Emory accounts, data, and systems.
Phishing Red Flags in This Email
- Urgency & Fear
- “Your account will be deactivated” pressures the recipient into acting without thinking.
- Suspicious Link
- Directs to a Google Form (forms.gle/...), which is not an official Emory domain.
- Official Emory notices always point to .emory.edu or .emoryhealthcare.org sites.
- Awkward Grammar
- Phrases like “transfer of the concerned account holder” are unprofessional and not consistent with real Emory IT messaging.
THE BAIT:
Trick users into entering their Zoom or Emory credentials on a fake verification site.
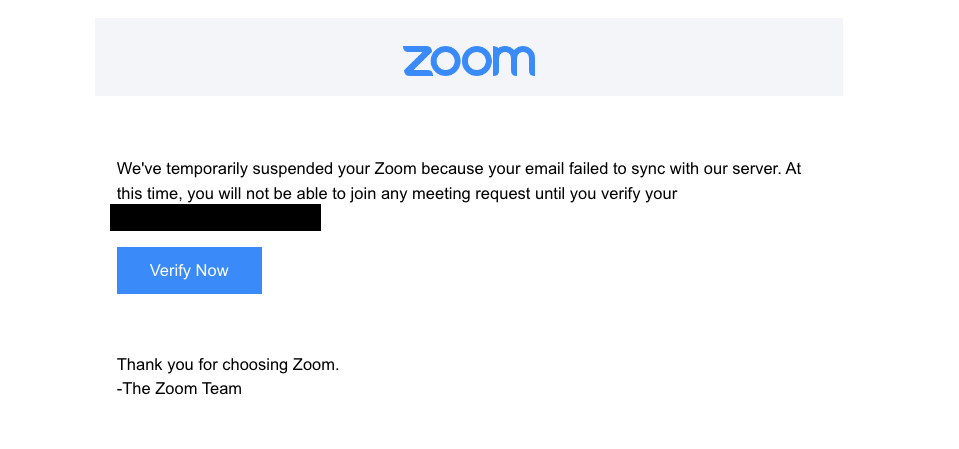
This is an attempt to trick the recipient into clicking the “Verify Now” link, which likely leads to a fake login page.
Type of Phishing Attack
- Credential Harvesting via Brand Impersonation
- Goal: Trick users into entering their Zoom or Emory credentials on a fake verification site.
- Method: Spoofs Zoom branding and adds urgency to lure clicks.
- Risk: Attackers gain access to user accounts, which can then be exploited for further compromise.
Phishing Red Flags in This Email
- Brand Impersonation
- Uses Zoom’s logo and style, but the sender address is not from @zoom.us or @emory.edu.
- Urgency & Service Disruption
- Claims your account is suspended and you can’t join meetings until you act, to create panic.
- Suspicious Call-to-Action
- The “Verify Now” button leads to a non-Zoom, non-Emory site. Real Zoom emails only link to zoom.us.
- Unusual Targeting
- Mentions a specific Emory email address, which is uncommon in real service alerts.
Key Takeaways for Phishing

Phishing can come from any compromised Emory email account. Never share your credentials with anyone.

Hover over links to check URLs before clicking (e.g., that Zoom emails come from @zoom.us or the Emory Zoom listserv).

Report suspicious emails through the Outlook “Report Phishing” button or by forwarding to abuse@emory.edu.